Noticed any anomalies online in the last week or so? Do you live in Europe or North America? Chances are if you said yes to both you are being impacted by the largest distributed denial of service (DDoS) ever recorded.
The anything-goes Dutch hosting provider CyberBunker, which has been accused of backing a DDoS disruption campaign against anti-spam site Spamhaus, as of Thursday morning found its own supposedly bulletproof website knocked offline, making it the apparent victim of a sustained DDoS attack.
That’s an ironic twist for CyberBunker, which has been one of the most outspoken proponents — and, some have alleged, sponsors — of a week-long series of massive DDoS attacks against Spamhaus.
Who are CyberBunkers?
CyberBunker is a Dutch company that, according to its website, hosts “services to any Web site ‘except child pornography and anything related to terrorism'”. It has hosted The pirate bay since October 2009 and Wikileaks since 2010. It also allegedly hosts spam sites.
Spamhaus is responsible for a number of very widely used anti-spam DNS-based Blocklists (DNSBLs) and Whitelists (DNSWLs). Many internet service providers and Internet networks use these services to reduce the amount of spam they take on. The Spamhaus lists collectively protect over 1.77 billion e-mail users, according to Spamhaus’ web page (November 2012) and are estimated to block 80 billion spam emails per day globally on the internet (almost 1-million spam emails per second). Like all DNSBLs, their use is considered controversial by some.
What is the issue between CyberBunkers and Spamhaus?
In October, 2011, Spamhaus identified CyberBunker as providing hosting for spammers and contacted their upstream provider, A2B, asking that service be cancelled. A2B initially refused, blocking only a single IP address linked to spamming. Spamhaus responded by blacklisting all of A2B address space. A2B capitulated, dropping CyberBunker, but then filed complaints with the Dutch police against Spamhaus for extortion.
March 2013…………
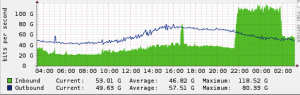
Spamhaus added CyberBunker to its blacklist. Shortly afterwards a distributed denial of service (DDoS) attack of previously unreported scale (peaking at 300 gigabits per second; an average large-scale attack might reach 50 Gbps, and the largest previous publicly reported attack was 100 Gbps) was launched against Spamhaus’s Domain Name System (DNS) servers exploiting a known vulnerability of DNS[9]; as of 27 March 2013 the attack had lasted for over a week. Steve Linford, chief executive for Spamhaus, said that they had withstood the attack. Other companies, such as Google, had made their resources available to help absorb the traffic[9]. The attack was being investigated by five different national cyber-police-forces around the world. Spamhaus alleged that Cyberbunker, in cooperation with “criminal gangs” from Eastern Europe and Russia, was behind the attack; Cyberbunker did not respond to the BBC’s request for comment on the allegation.
What Exactly Happenned?
A little over a week ago a questionable internet hosting provider in The Netherlands called Cyberbunker took umbrage with SpamHaus, an non-profit organization that was founded in 1998 to take on spammers and the internet hosts who profit from their activities.
Cyberbunker takes its name from the former NATO bunker that the company operates out of. Not surprisingly they appear to be offline at the moment, whether that is due to a DDoS attack or other circumstances is difficult to discern.
Cyberbunker caters to customers who are unwanted by or afraid to use traditional web hosts because of the activities they are involved in.
Their target markets include copyright abusers, spammers, malware malcontents and just about any other type of activity… Except child porn and terrorism (thank God for that).
Because of the nature of Cyberbunker’s traffic Spamhaus decided to add Cyberbunker’s IP addresses to their blacklist of dodgy, spammy hosts. Cyberbunker proceeded to attempt to take Spamhaus offline in retribution.
How big is the attack?
At times it has been reported to be as large as 300 gigabits per second. Traditionally even large botnets are only able to deliver hundreds of megabits or a few gigabits per second.
What is so special about this attack? It is a large scale DNS reflection attack that takes advantage of misconfigured DNS servers to amplify the power of a much smaller botnet.
Cloudflare, an anti-DDoS provider, was hired by Spamhaus to protect their systems (which remain online). They have reported that in a much smaller attack in late 2012 more than 68,000 DNS servers were utilized in a single attack.
How big is this problem?
The Open Resolver Project reports more than 21.7 million insecure/misconfigured DNS servers on the IPv4 internet today.
What is problem for normal users and tier 1 service providers?
Many of the primary internet backbones (“tier 1 service providers”) are being overwhelmed by the volume of traffic from this attack. This can make access to some sites slow or even temporarily impossible during peak attack volumes. These sites and providers could be considered collateral damage.
Media Release For This Attack
CyberBunker, which says it’s headquartered in an ex-NATO “former military nuclear warfare bunker that is currently utilized as bulletproof data center,” made a name for itself by advertising services to any website “except child porn and anything related to terrorism.” The company previously gained notoriety for providing hosting to the Russian Business Network cybercrime gang, which the FBI ultimately helped dismantle.
Lately, CyberBunker has backed the so-called Stophaus.com campaign, which is designed to knock anti-spam organization Spamhaus offline. As of Thursday morning, however, the Stophaus.com website was also unreachable, with the homepage resolving to a page that read only “database error.”
CyberBunker spokesman Kamphuis claimed that his company isn’t responsible for the DDoS attacks that were first launched last week against Spamhaus. “Well, it’s not us, it’s a group of Internet providers which goes under the name Stophaus.com. It’s basically a collective of a lot of people and Internet providers, and they’ve had previous issues or current issues with Spamhaus,” Kamphuis told broadcaster Russia Today Wednesday. “Spamhaus pretends to be spam fighters, but effectively they’re just a censorship organization which worked itself into a position where they can just look at a website and shut it down,” he said.
But security expert Dan Kaminsky says the bottom line here is that there are three problems that allow for this type of nefarious activity on the Internet: “We can’t authenticate, we can’t write secure code, and we can’t bust the bad guys,” he says.
“There are people in this world who think they have the God-given right to sell you Viagra, and anyone who gets in their way must be punished. But there are others of us who respectfully disagree,” Kaminsky added.
The attackers not only went after CloudFlare’s direct peers, but the exchanges it connect with –the London Internet Exchange, the Amsterdam Internet Exchange, the Frankfurt Internet Exchange, and the Hong Kong Internet Exchange. The London Exchange was the hardest hit, according to CloudFlare.
“Once the attackers realized they couldn’t knock CloudFlare itself offline even with more than 100Gbps of DDoS traffic, they went after our direct peers. In this case, they attacked the providers from whom CloudFlare buys bandwidth. We, primarily, contract with what are known as Tier 2 providers for CloudFlare’s paid bandwidth. These companies peer with other providers and also buy bandwidth from so-called Tier 1 providers,” Prince wrote in a blog post today. “Over the last few days, as these attacks have increased, we’ve seen congestion across several major Tier 1s, primarily in Europe where most of the attacks were concentrated, that would have affected hundreds of millions of people even as they surfed sites unrelated to Spamhaus or CloudFlare. If the Internet felt a bit more sluggish for you over the last few days in Europe, this may be part of the reason why.”
How to Generate a 75Gbps DDoS attacks
A blog post by CloudFlare, written last week before the latest run of attacks, explains the mechanism of the attack against Spamhaus and how it can be usde to amplify packet floods.
The basic technique of a DNS reflection attack is to send a request for a large DNS zone file with the source IP address spoofed to be the intended victim to a large number of open DNS resolvers. The resolvers then respond to the request, sending the large DNS zone answer to the intended victim. The attackers' requests themselves are only a fraction of the size of the responses, meaning the attacker can effectively amplify their attack to many times the size of the bandwidth resources they themselves control.
In the Spamhaus case, the attacker was sending requests for the DNS zone file for ripe.net to open DNS resolvers. The attacker spoofed the CloudFlare IPs we'd issued for Spamhaus as the source in their DNS requests. The open resolvers responded with DNS zone file, generating collectively approximately 75Gbps of attack traffic. The requests were likely approximately 36 bytes long (e.g. dig ANY ripe.net @X.X.X.X +edns=0 +bufsize=4096, where X.X.X.X is replaced with the IP address of an open DNS resolver) and the response was approximately 3,000 bytes, translating to a 100x amplification factor.
Courtesy :
http://www.smh.com.au/it-pro/security-it/spam-dispute-becomes-largest-cyber-attack-in-history-of-the-internet-20130327-2gtw1.html
http://www.informationweek.com/security/attacks/ddos-spam-feud-backfires-bulletproof-cyb/240151895